Organizations have traditionally viewed vulnerability scanners as a tactical product, largely commoditized and only providing value around audit time. But with limited resources...
Choosing a solution for Vulnerability Management (VM) is a critical step toward protecting your organization’s network and data. Without proven, automated technology...
New network vulnerabilities appear constantly and the ability for IT security professionals to handle new flaws, fix misconfigurations and protect against threats requires...
This Windows 8 guide is a comprehensive collection of answers to the most popular questions asked over the past three years. It's roughly 100 pages of simple, easy to understand...
For the modern organization, the processes and programs related to Travel and Entertainment (T&E) expenses are growing more complex, as the modern T&E lifecycle involves a...
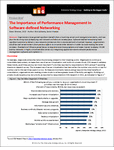
Software-defined networking holds significant promise to deliver a new network architecture that is abstracted and virtualized; however, organizations would be well served...